Force remote logoff after idle time
Watch how IT administrators can set an automatic forced logoff, on all locked or open machines, after a certain idle time with UserLock. This includes remote desktop sessions opened by the domain user.
Updated September 5, 2023)
Fast and fluid access to shared workstations is key to their utility, but managing this access can be a challenge. Watch how UserLock makes it easier to force a remote logoff after a pre-set amount of idle time.
Whether your users are call center agents, hospital clinicians, reception desks or student computer labs, the problem is often the same. Users log in and never log off. They simply lock the workstation and walk away. Once you have multiple users just clicking "Switch User" to login, there are enough random applications running in the background from all these idle users that the system slows to a crawl.
Worse still, rather than locking, they just leave their session open. Forgotten sessions left open on shared workstations means user accounts are now at risk (high risk!) of being compromised.
With the ability to remotely force a logoff for idle users, you can significantly lower the risk of these user accounts being compromised.
Since shared workstations are an entry point to your organization’s data resources, you'll want to make sure they have the best security configuration.
With UserLock, IT administrators can set an automatic forced logoff, on all locked or open machines, after a certain idle time. This includes remote desktop sessions opened by the domain user. Access to data and resources is now better secured, resources freed up and time saved for IT from having to deal with various issues.
What follows is a video transcript from the video linked above.
In this video I’m going to show you how UserLock can be configured to allow you to automatically log off, lock machines, after an idle time.
So the first thing we need to do is make sure that on the target machines we have the screen saver option “on resume display logon screen.”
This can be enabled through a Microsoft GPO setting.
Back in the UserLock console we’re going to go to the properties of the agent distribution and here we’re going to check to “consider screen saver time as locked time,” that way in Userlock we can recover the events as a locked session.
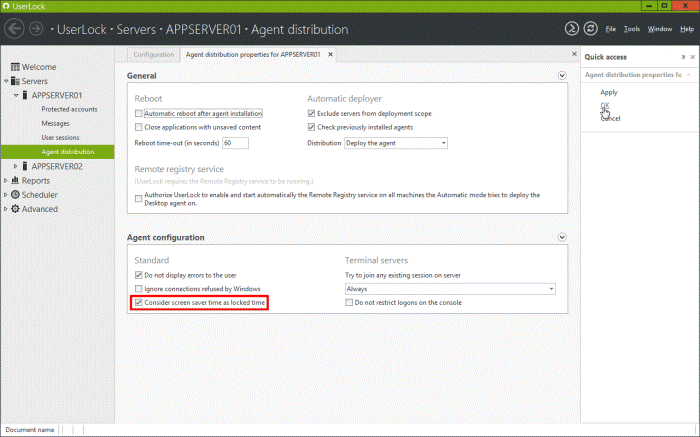
Click here to apply the new setting and this will be effective on the target machines at the next reboot or we can force it to be effective immediately by restarting the UserLock agent service (ULAgentService) on the target machine.
So once you’ve done that setting we need to now select the user accounts for which we’d like this setting to be enabled.
So we’re going to protect a new account, we can do this at the user, group or OU level. I’m going to do this for Active Directory group “everyone."
I create my protected account and then by simply double-clicking on the protected account I have access to the properties and all of the settings and restrictions that I can set for this protected account.
So we’re going to go down to hour restrictions and here we have “Maximum locked time.” So once the screensaver has been enabled, we’re going to put in the amount of time that we will allow the computer to be locked before we force a logoff. So for example we can put 10 minutes.
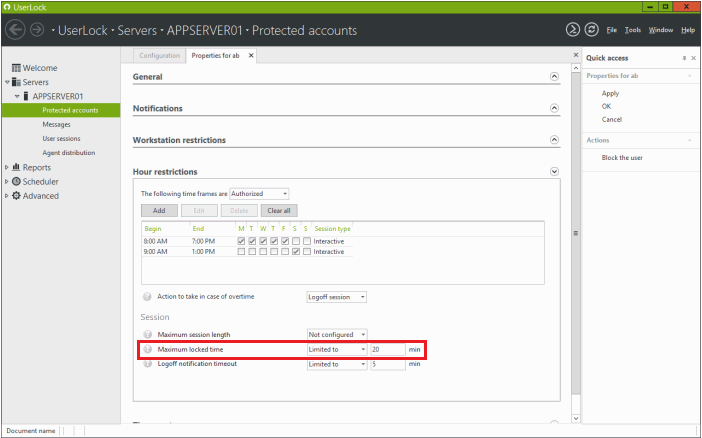
By default the end user is going to receive a logout notification, that’s by default one minute before the log off. If we’d like to allow a little bit more time — if they’d like to bypass the logoff — we can change that here. So we can apply these settings.
So that’s it that’s how we can configure a forced logoff of computers that are open after a certain amount of idle time to free up workstations and to reduce unnecessary use of resources on your network.
Note:
The "Session" options are supported by interactive session types (workstation and terminal).
The logoff initiated by these options is forced. Any unsaved documents will be lost.
Direct from the console, UserLock can interact remotely with any session, at any time. This includes a forced logoff to several machines at once or blocking a user with a single click.
Read how the Architectural Technology Department of the NYCCT (New York City College of Technology) stopped forgotten Windows sessions to secure their network and free up resources.
If you're curious about other use cases that involve managing user logins, you can find more here.
)
)
)
